
CEO Jim Gillespie Talks With Technical.ly Pittsburgh
February 2, 20232023 is the Year of AI
March 2, 2023
CEO Jim Gillespie Talks With Technical.ly Pittsburgh
February 2, 20232023 is the Year of AI
March 2, 2023NIST Cyber Framework Adds Sixth Function
NIST Adds Sixth Function to Framework
The National Institute of Standards and Technology (NIST) offers one of the most widely used cybersecurity frameworks in the world.
So, it's a big deal in cyber circles that NIST-CSF is poised to add a new function — Govern — to its well-known, five-part framework.
An Evolving Framework
The U.S. Commerce Department institute developed NIST-CSF Version 1.0 in February 2014 to help federal agencies strengthen their cybersecurity preparedness.
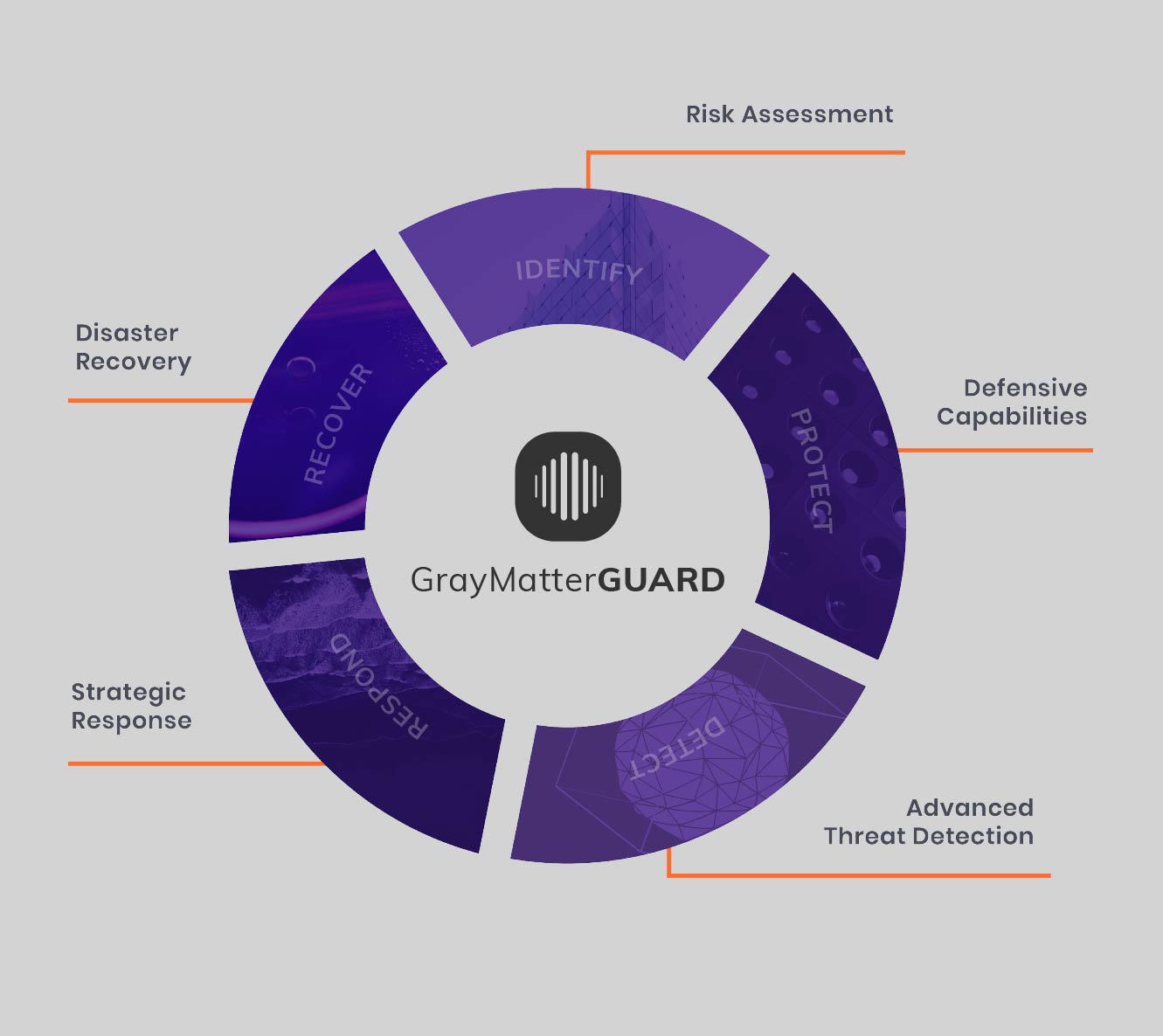
It has since grown to become a go-to resources for private and public organizations developing a cybersecurity program around the five core functions of NIST-CSF: Identify, Protect, Detect, Respond, Recover.
The proposed NIST-CSF Version 2.0 is the first time NIST would add a function, highlighting the importance of cyber governance and planning.
Industrial Cybersecurity
GrayMatter's Industrial Cybersecurity offering is based on the functions of NIST-CSF. NIST isn't the only framework out there, but it is among the only "open source" resources of its kind, meaning anyone can view and use its source material, NIST doesn't require special certifications to begin implementing it and the process of updating the framework is open to public comment.
NIST received "substantial input" from stakeholders that said govern deserved to become its own function.
"This new crosscutting function will highlight that cybersecurity governance is critical to managing and reducing cybersecurity risk. Cybersecurity governance may include determination of priorities and risk tolerances of the organization, customers, and larger society; assessment of cybersecurity risks and impacts; establishment of cybersecurity policies and procedures; and understanding of cybersecurity roles and responsibilities."
– NIST-CSF Ver. 2.0
Governance was previously part of the Identify function of NIST. Now that it's set to be its own category, the hope is that organizations will prioritize cybersecurity risk management, cyber assessments and other concerns such as cybersecurity supply chain management.
Getting Started
The good news is that no one has to wait for NIST to complete the update to its framework. Now is the best time to think about how your industrial organization is managing its cybersecurity.
GrayMatter has helped hundreds of companies evaluate how to protect their operational technology — the physical plant systems that run a facility and generate revenue. Many companies rely on third-party like GrayMatter to help them determine exactly what assets are connected to their network and how they're communicating.
What's more, a third party can provide valuable insights on how to prioritize cybersecurity precautions.
